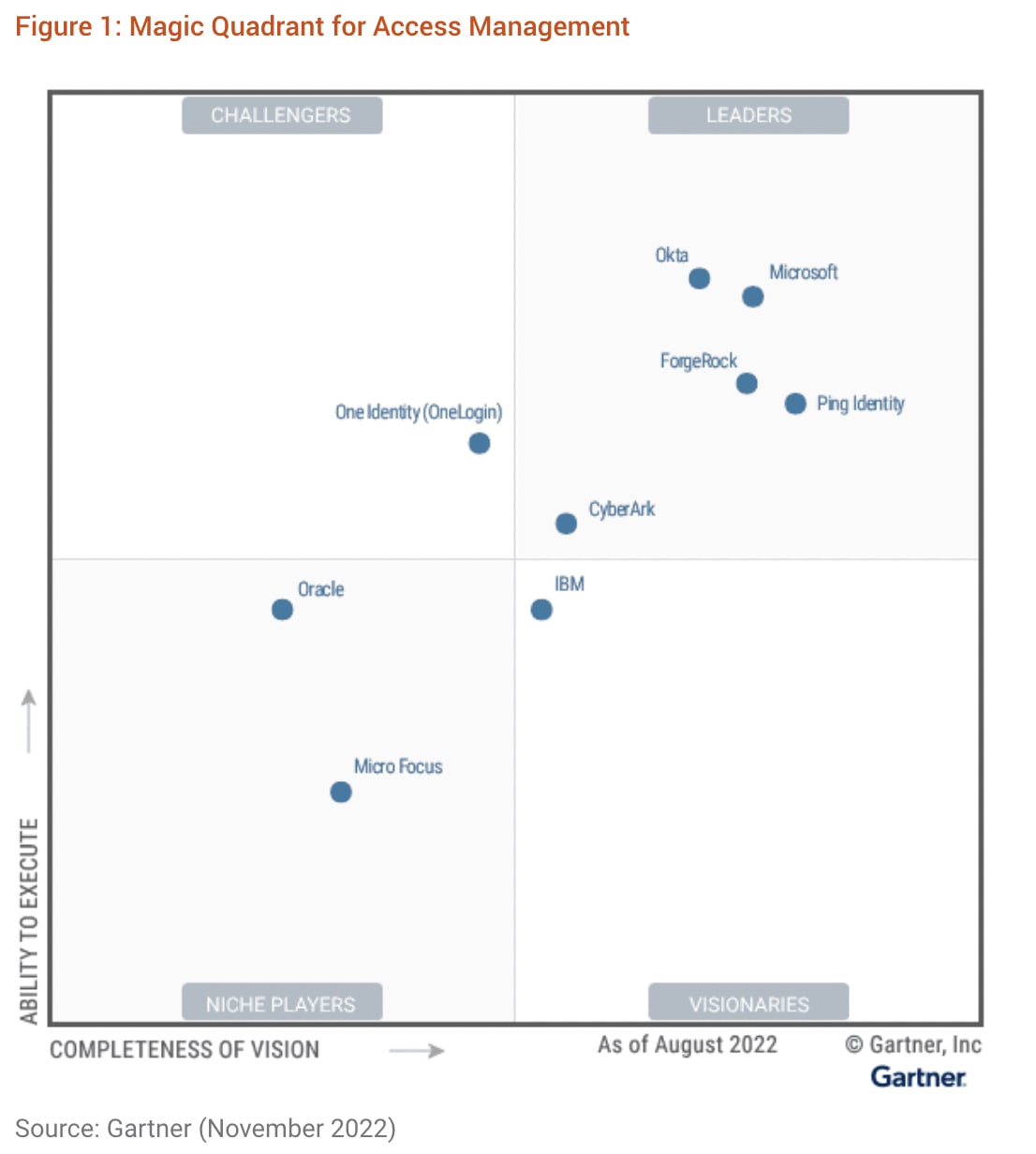
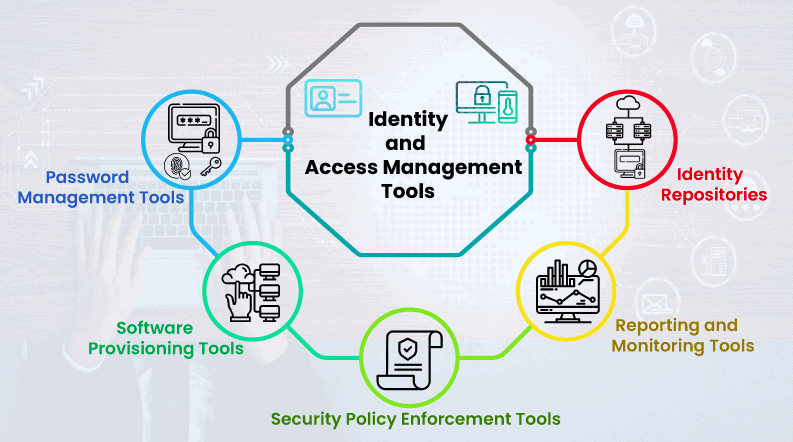
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
Iam Tools Gartner . This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
This Planning Guide Helps Security And Risk Management Technical Professionals Modernize Iam Architecture, Focus On Outcomes Over Tools, Address All Identities And Support A Strong Iam Program.
Iam tools gartner . By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
Iam Tools Gartner
Gartner Multifactor Authentication Trends
Source: diagramlistaneurisms.z14.web.core.windows.net
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
Insights from the Gartner Magic Quadrant for AI Applications in ITSM
Source: blog.invgate.com
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
7 Tips to Make Sense of the Gartner IAM Magic Quadrant Security Boulevard
Source: securityboulevard.com
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
Cisco Collaboration a Leader in 5 Gartner Magic Quadrant Reports
Source: blogs.cisco.com
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
IAM/SSO Provider Feature Okta Identity Management
Source: blog.pacifictimesheet.com
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Architecture of Identity Access Management in Cloud Computing
Source: www.geeksforgeeks.org
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
2024 Gartner® Magic Quadrant™ for PAM BeyondTrust… BeyondTrust
Source: www.beyondtrust.com
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Strata Identity on LinkedIn Strata mentioned in 2024 Gartner® Outage
Source: www.linkedin.com
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
Gartner Magic Quadrant 2024 Tealium
Source: tealium.com
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Top 5 identity & access management (IAM) tools for 2024 Cerbos
Source: www.cerbos.dev
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
Top 11 Identity & Access Management Tools Security Boulevard
Source: securityboulevard.com
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Gartner Identity & Access Management (IAM) Critical
Source: www.manageengine.com
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
The Gartner IAM Program Maturity Model Enterprise architecture
Source: www.pinterest.co.uk
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Guidance for Achieving IAM Resilience in a CloudFirst World Gartner
Source: www.gartner.com
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
IAM Gartner
Source: allidm.com
This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
Identity Management itcaps
Source: www.itcaps.net
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem.
Understanding Key Identity & Access Management Components Blog
Source: braxtongrant.com
This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
BizTechIdentity and Access Management Webinar
Source: www.slideshare.net
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This cohesive structure reduces identity sprawl and extends governance to the farthest endpoints of your iam ecosystem. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program.
Gartner Magic Quadrant for Identity Governance and Administration (2018
Source: www.51sec.org
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.
6 Identity and Access Management Trends to Plan for in 2022
Source: www.gartner.com
By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency. This planning guide helps security and risk management technical professionals modernize iam architecture, focus on outcomes over tools, address all identities and support a strong iam program. By unifying iam tools, including identity governance and administration (iga), access management (am), privileged access management (pam), and active directory management (ad mgmt), it ensures optimal functionality and efficiency.